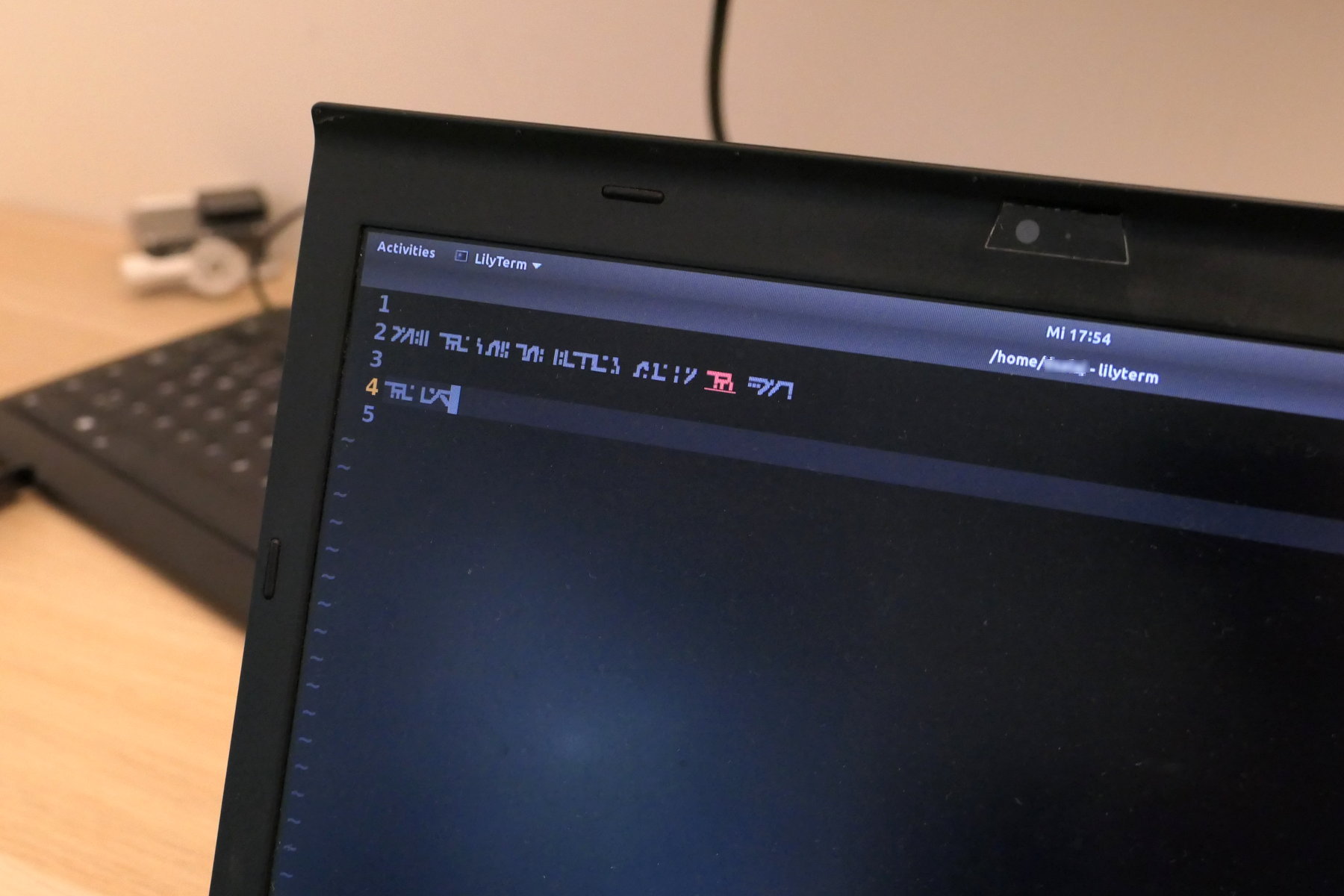
 Laptop screen with some text displayed using standard galactic alphabet font.
Laptop screen with some text displayed using standard galactic alphabet font.
Anyone that has learned anything about cryptography is familiar with Diffie–Hellman key exchange algorithm. This is one of the earliest algorithms to demonstrate the ability to exchange secret key and provide secure and encrypted communication, all through public (insecure) channel. It is a demonstration of how cryptography uses math to establish secure communication instead of relying on secure physical channels or trusted courier.
People familiar with these concepts (developers, cs students, and such) will openly bash and ridicule the concept of security through obscurity as some ancient and outdated tool that only an uneducated individual would even consider using. It is also often used as a synonym for bad implementations of security, implying that it is only secure as long as the attacker does not know the implementation. Here I want to counter these arguments by showcasing that security through obscurity is very much a useful paradigm if only applied on the right usecase.
For every tool there is a job, and not knowing how to pick a tool for the job doesn’t make the tool bad, it just implies that the user is incompetent. Now days the term “security through obscurity” is almost exclusively used by developers and computer scientist to sarcastically comment on insecure software implementations. Most however don’t actually realize that there exists a historic but very practical application of security through obscurity.
Think of Caesar cipher, it is super simple method to encrypt text. The downside is that it is super easy to decipher if the attacker has access to the whole message and a computer or some time. But what about the cases were the attacker does not have the access to the message? Or if the attacker is not really an attacker but only a person next to you impolitely glancing at your screen? Well in that case Caesar cipher would work perfectly and you would have full privacy of your computer screen in any crowded space.
Now the downside for me is that learning and using the Caesar cipher is not easy, and it’s extremely confusing since the shifted alphabet can produce some string reminiscent of some words etc. which makes reading extremely hard. Another downside is that you need to actually run a script to decipher your text when you decide to share the content or process it. Finally, the spellchecker or similar tools just won’t work, and you will type much slower since your old muscle memory is useless.
As an alternative I have found that simply switching fonts gives you all the benefits with no downsides of Caesar cipher. You also get to have fun with choosing your own obscure font. It will take some time to learn all the symbols to be able to read your text, but at least you will look uber-cool typing. I have picked the Standard Galactic Alphabet (originating from video game Commander Keen). It was super fast to pick it up (one day) and I actually started handwriting it in my notebook sometimes. The photos bellow demonstrate the difference between using obscure and regular fonts.
 Laptop screen with some text displayed using standard galactic alphabet font.
Laptop screen with some text displayed using standard galactic alphabet font.
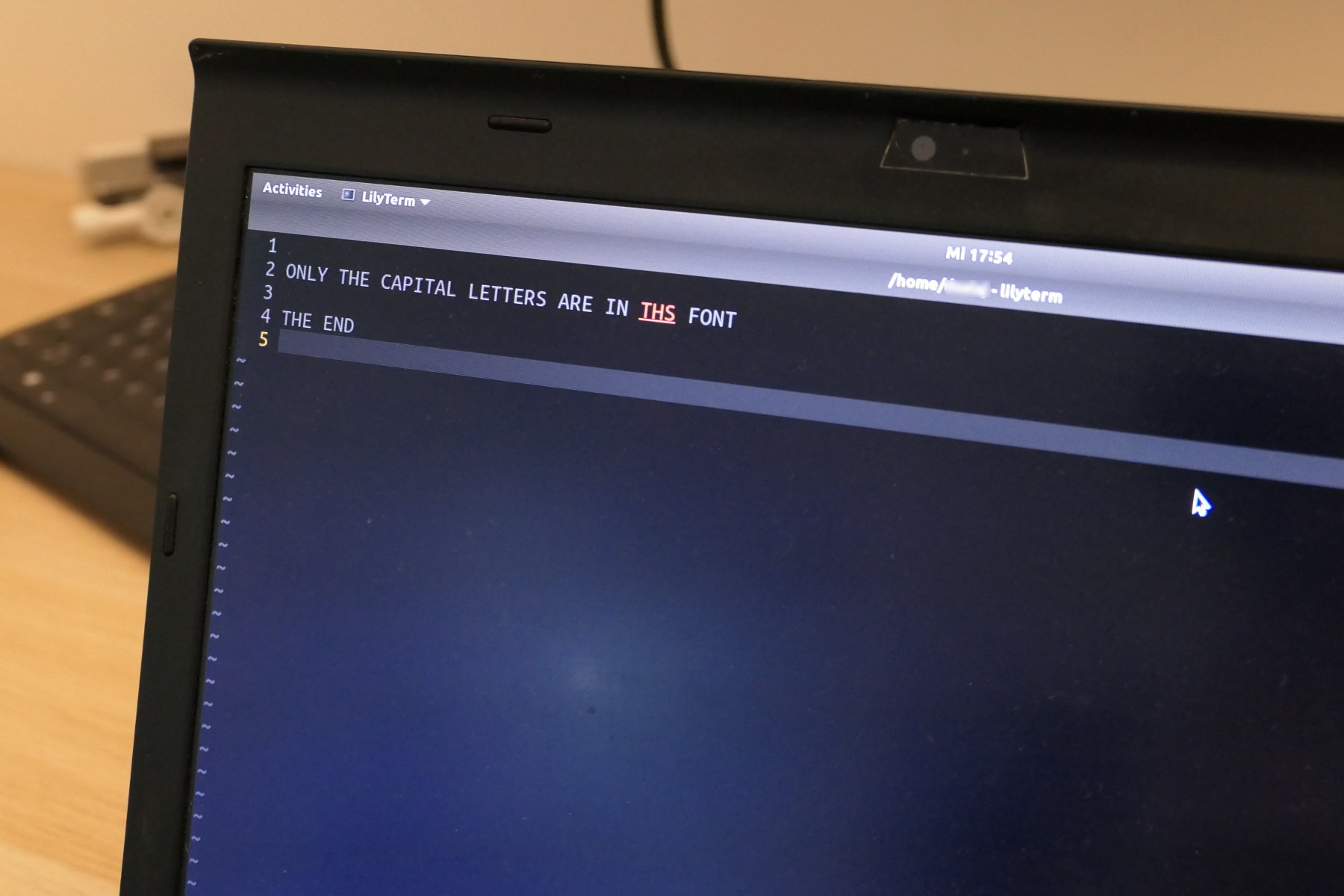 Laptop screen with some text displayed using regular font.
Laptop screen with some text displayed using regular font.
So there you go! Through obscurity you can obtain the total privacy from surrounding observers when writing on or in your notebook. And this is just one use case, there is probably plenty more that are waiting to be explored.